Introduction
Following on from Part 1, you should now have an AudioCodes SBC up and running in Azure. This article will cover any Azure specific setup to allow Teams Direct Routing to function.
For Direct Routing configuration you can follow my earlier blog post for instructions.
Note: In Azure, we are using a single NIC, so the “LAN” and “WAN” NIC mentioned is the same interface, so bear this in mind when configuring Media Realms, SIP interfaces etc.
Once you have a SIP trunk and Direct Routing configured, you are in a position to follow on
Step 1 - Configure Azure NSG
To allow communication between your SIP trunk and Microsoft Teams, we need to allow the ports through the NSG. The NSG is essentially a list of rules on which traffic is or isn’t allowed through from the Internet (or other networks) - not dissimilar to a firewall.
Before we can add rules, we need to know what media and signalling ports the SBC is configured to use.
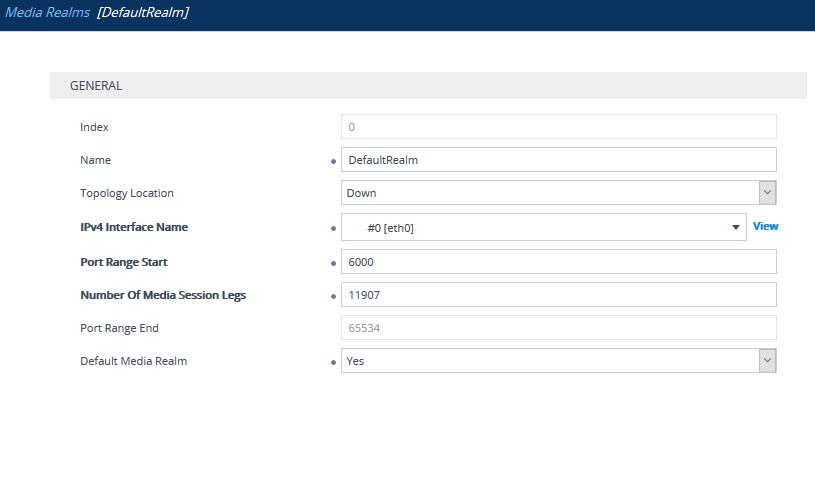
For Media Ports: Under Signaling and Media > Core Entities > Media Realms, check the realm that is assigned to the IPv4 interface. In my case I have the DefaultRealm, it’s created quite a large range, but you could make this smaller if needed:
For Signaling Ports: Check the UDP, TCP and TLS ports in the SIP Interfaces of Teams and SIP Trunks:
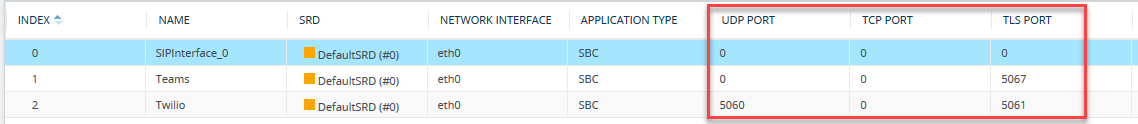
So, in my case I need to allow ports 5060 UDP and 5061, 5067 TCP (TLS) for signalling and 6000-65534 UDP for media:
| **Source IP** | **Destination IP** | **Destination Ports** | **Comment** |
| SIP Trunk | SBC IP | 5060 UDP | Inbound UDP Signaling from SIP Trunk |
| SIP Trunk | SBC IP | 5061 TCP | Inbound TCP (TLS) Signaling from SIP Trunk |
| SIP Trunk | SBC IP | 6000-65534 UDP | Inbound Media from SIP Trunk |
| Teams Direct Routing | SBC IP | 5067 TCP | Inbound TCP (TLS) Signaling from Teams Direct Routing |
| Teams Direct Routing | SBC IP | 6000-65534 UDP | Inbound Media from Teams Direct Routing |
| SBC IP | SIP Trunk | 5060 UDP | Outbound TCP (TLS) Signaling to SIP Trunk* |
| SBC IP | SIP Trunk | 5061 TCP | Outbound TCP (TLS) Signaling to SIP Trunk* |
| SBC IP | SIP Trunk | 10000-20000 | Outbound Media to SIP Trunk* |
| SBC IP | Teams Direct Routing | 5061 TCP | Outbound TCP (TLS) Signaling to Teams Direct Routing* |
| SBC IP | Teams Direct Routing | 49152-53247 UDP | Outbound Media to Teams Direct Routing* |
* Outbound rules are only needed if the behaviour of NSG is to block unspecified traffic.
The ports used above for the SIP trunk are specific to the SIP trunk I’m using (Twilio). You will need to get these from your SIP trunk provider.
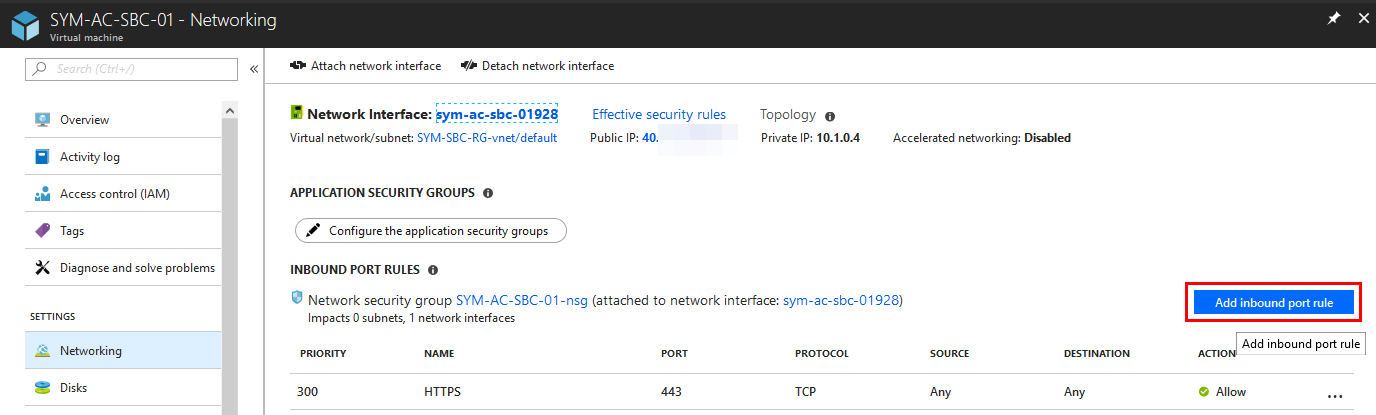
With that noted down, let’s add some rules to the NSG. These can be found on the Azure Portal. If you go to the SBC you deployed, under Networking, you can add Inbound Port rules:
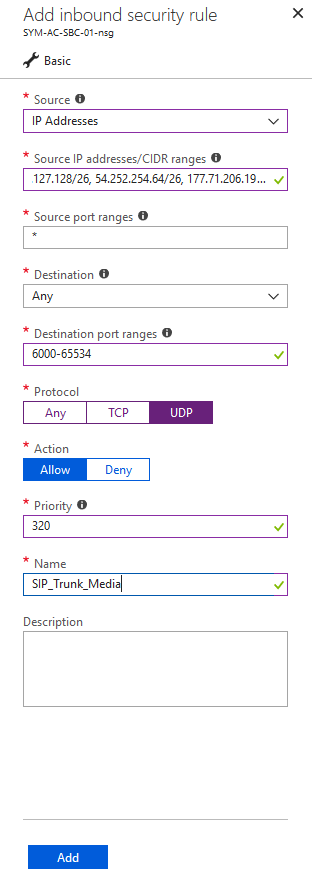
SIP Trunk
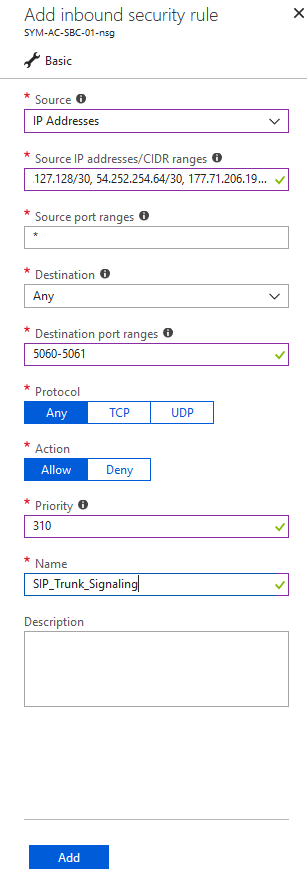
In my scenario, I’m using a Twilio SIP trunk, so I will only allow their IP addresses through for Signaling and Media:
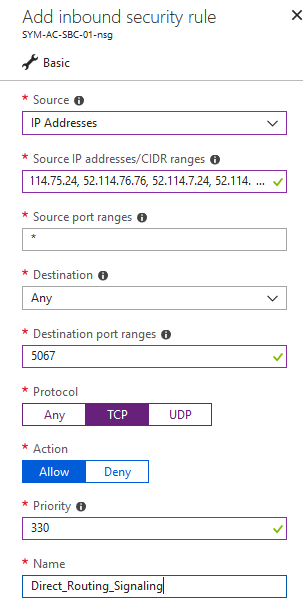
Teams Direct Routing
For Direct Routing, we need to again allow signalling ports from the Teams SIP Proxy IPs, which are:
- 52.114.148.0
- 52.114.132.46
- 52.114.75.24
- 52.114.76.76
- 52.114.7.24
- 52.114.14.70
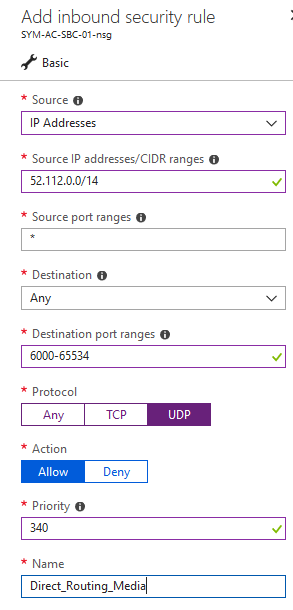
For media ports, we need to allow the single subnet of 52.112.0.0/14:
Note: The NSG will allow all outbound traffic by default. If you want to lock this down you can, but will need to create rules to allow the traffic outbound.
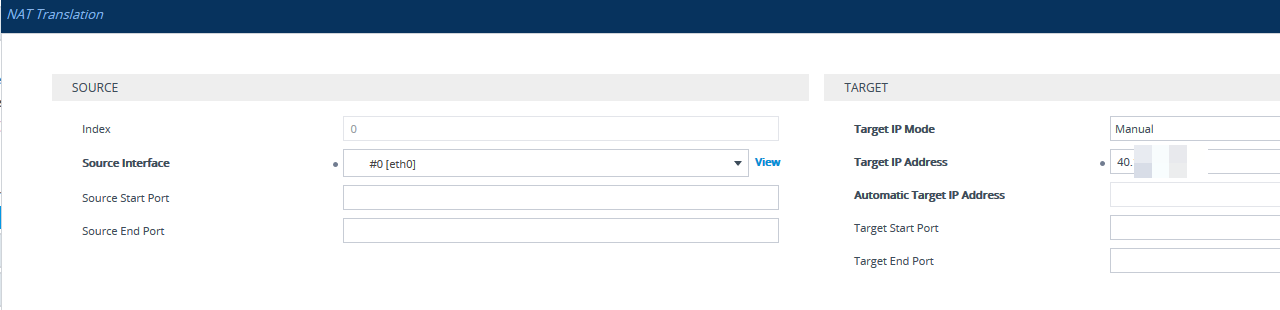
Step 2 - Configure NAT Address on SBC
The NSG will NAT, but it is not SIP-aware, you will need to specify the NAT address on the SBC, so it sends the Azure public IP instead of its own internal address. You can set this under Setup > IP Network > Core Entities > NAT Translation
With all that in place, you should be able to make and receive calls within Teams.