Configuring Direct Routing with dual WAN connectivity
One project I have been working on recently at Symity is a global roll out of Teams Direct Routing. This has resulted in SBCs being installed in different configurations based on local connectivity and requirements. One such requirement is where sites have multiple internet connections for resilience - can the SBC make use of this? It makes perfect sense especially when using cloud-based service – if one ISP has an issue, you want to be able maintain service with the other.
When factoring this into the design of a Direct Routing solution it became apparent dual internet connections could be used for this.
In the diagram below there is a single SBC connected to two ISPs with different public IP addresses assigned to the SBC. Two routes are then configured within Office 365 to reach the SBC. Obviously in this diagram, there is a single point of failure in the SBC, but that could be remedied with a HA pair of SBCs.
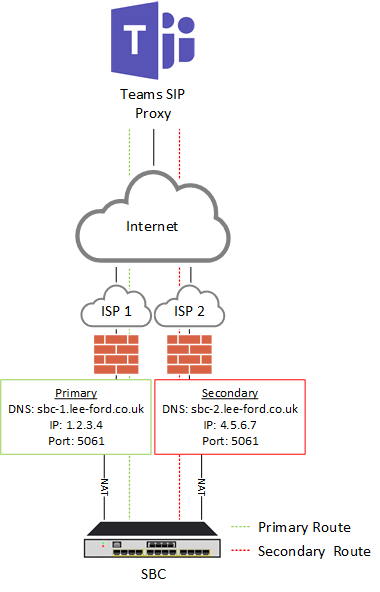
As far as Office 365 is concerned, you are configuring two separate PSTN Gateways that happen to terminate on the same SBC. This is achieved my using two different FQDNs when configuring the PSTN Gateways.
Configuration
The configuration doesn’t differ massively from a standard Direct Routing setup, but I will highlight the steps required.
DNS
As mentioned earlier, you will configure two FQDNs in Office 365 for the two PSTN Gateways. So, you will need to create two A records in external DNS – one to each public IP address the SBC will be using.
| A Record | Destination IP Address |
|---|---|
| sbc-1.lee-ford.co.uk | 1.2.3.4 |
| sbc-2.lee-ford.co.uk | 4.5.6.7 |
Configure SBC
I won’t go into massive detail on to configure this as it will vary between vendors – I am not even sure if this works with all vendors! In this scenario I have used an AudioCodes SBC and assigned two DMZ IP addresses to it. A public IP address from each ISP is then NAT’d to the corresponding DMZ IP address.
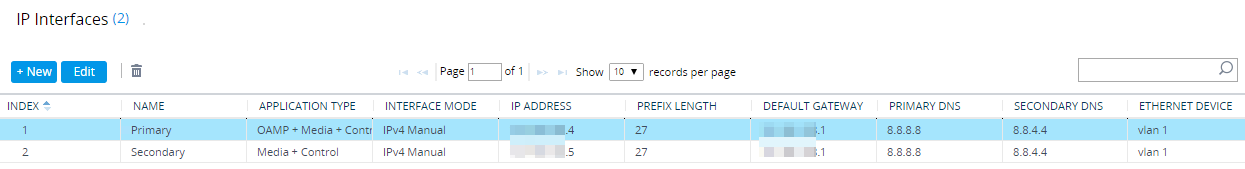
You could also configure two public IP address direct to the SBC, but this is usually seen as ‘unsecure’ by security teams as it bypasses a corporate firewall. As far as AudioCodes goes, each IP address will need its own SIP interface and media realm to ’listen’ on each IP address.
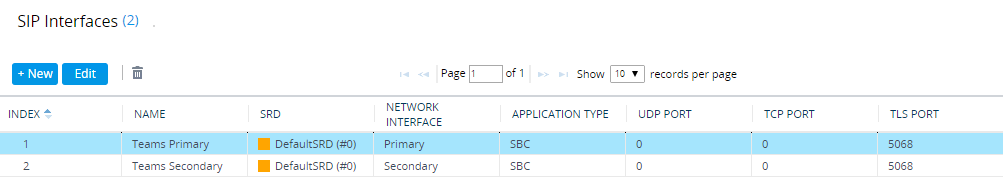
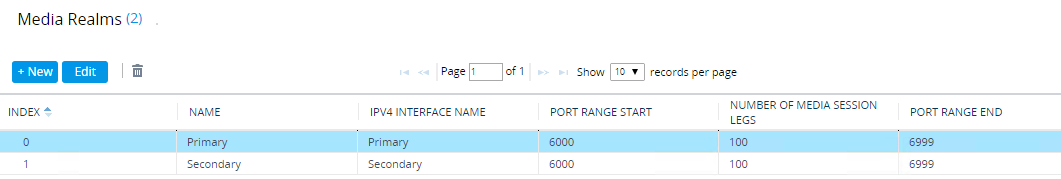
For AudioCodes, the Teams Proxy Sets and IP Groups are configured on both interfaces too.
Certificate
The SBC will need to have a certificate with both FQDNs in the SAN list. You may also be able to use a wildcard certificate (if FQDNs are on the same domain), but I have not tried this.
CN=sbc-1.lee-ford.co.uk
SAN=sbc-1.lee-ford.co.uk
SAN=sbc-2.lee-ford.co.uk
Configure Direct Routing
At this stage you should have DNS records created, certificate installed, and the SBC configured. You can now add the PSTN Gateways and the routing into Office 365.
You will need to connect to Skype Online PowerShell.
PSTN Gateways
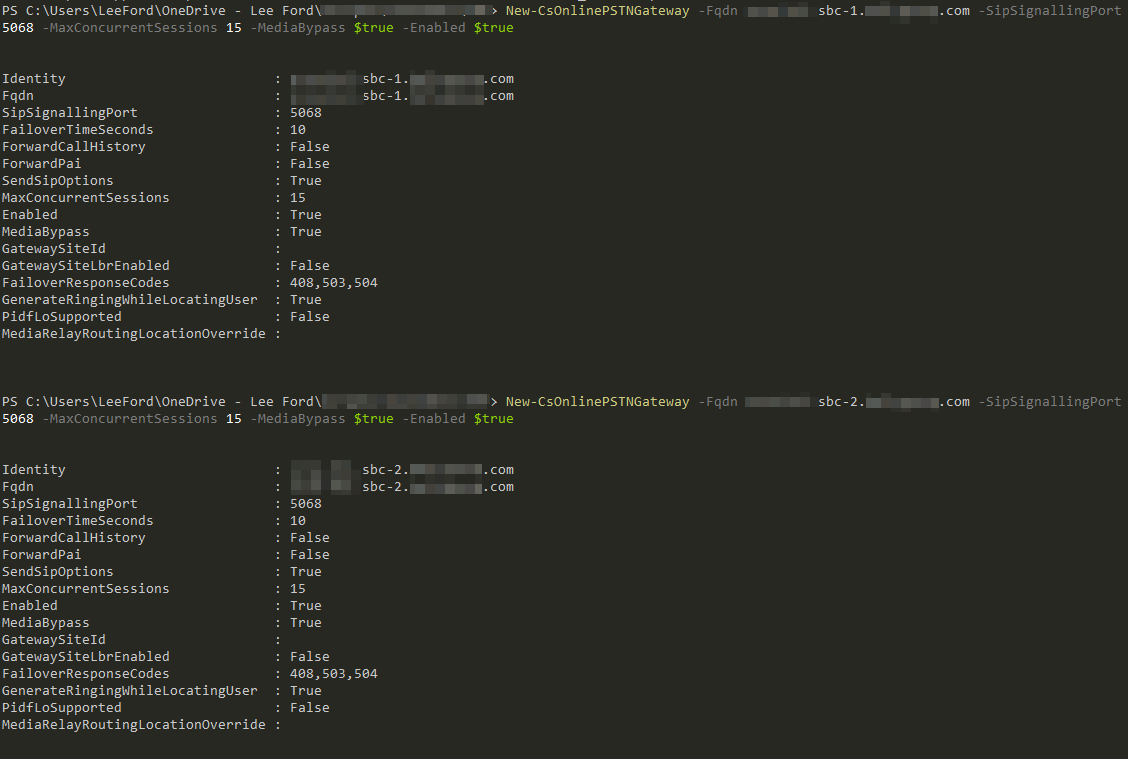
Once connected, start by adding both PSTN Gateways:
New-CSOnlinePSTNGateway -Fqdn sbc-1.lee-ford.co.uk -SipSignallingPort <port> -MaxConcurrentSessions <sessions> -Enabled $true
New-CSOnlinePSTNGateway -Fqdn sbc-2.lee-ford.co.uk -SipSignallingPort <port> -MaxConcurrentSessions <sessions> -Enabled $true
PSTN Usage
If you haven’t created a PSTN Usage yet, create one:
Set-CSOnlinePSTNUsage -Identity Global -Usage @{Add="<PSTN Usage>"}
Online Voice Routes
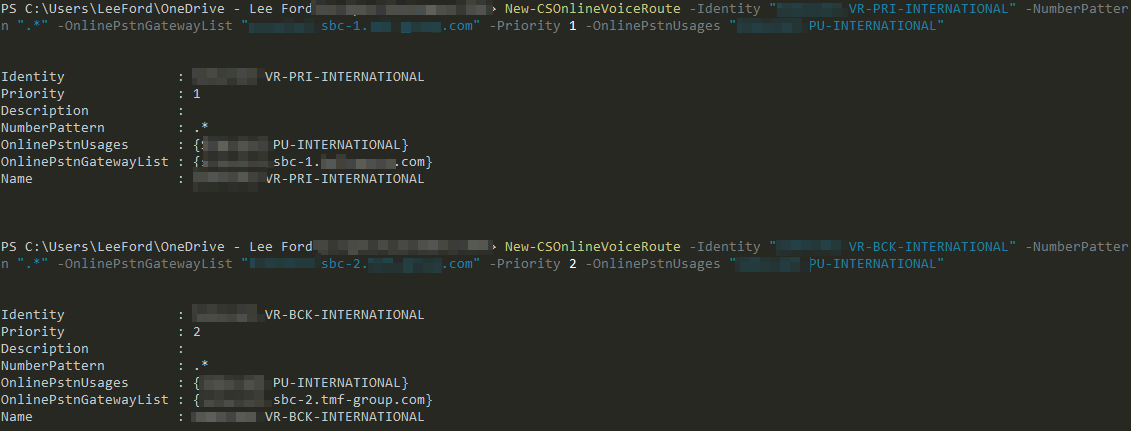
For every Online Voice Route you require e.g. local, national, international create two – one for each PSTN Gateway. Note the priority of each route:
New-CSOnlineVoiceRoute -Identity "CATCH-ALL-PRI" -NumberPattern "*," -OnlinePSTNGatewayList "sbc-1.lee-ford.co.uk" -Priority 1 -OnlinePSTNUsages <PSTN Usage>
New-CSOnlineVoiceRoute -Identity "CATCH-ALL-SEC" -NumberPattern "*," -OnlinePSTNGatewayList "sbc-2.lee-ford.co.uk" -Priority 2 -OnlinePSTNUsages <PSTN Usage>
In my example I have just created a single “catch all” route for each PSTN Gateway to show how this is done, but this is not always recommended.
A question you may have is why not just add both to PSTN Gateways to a single Online Voice Route. You could do that, but I wanted to force using the primary PSTN Gateway (not load balance) where possible and only use the secondary if needed.
Online Voice Routing Policy
Lastly, if you haven’t already, add the PSTN Usage to the Online Voice Routing Policy you will assign to the users.
New-CSOnlineVoiceRoutingPolicy <Policy Name> -OnlinePSTNUsages <PSTN Usage>
Wrap Up
At this stage you should have two PSTN Gateways configured to a single SBC. The primary ISP connection should be used where possible. If that is unavailable traffic will route via the secondary ISP connection. For incoming calls, this will rely on how you configure the SBC routing.
